With the OAuth 2.0 client
credentials flow, exchange of consumer key and consumer secret defined in the
connected app happens for generating an access token and hence it’s important
to understand its security risks. With this flow enabled, any person or app
that has access to your connected app’s consumer key and consumer secret can
get an access token. Maintain security by periodically changing your consumer
secret, and change it immediately if it becomes compromised.
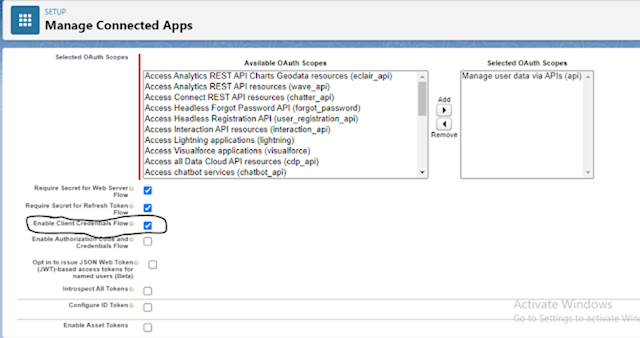
To enable the client credentials
flow for your connected app.
From Setup, in the Quick Find box,
enter Apps, and then select App Manager.
Find your connected app, click
Action dropdown, and then select Edit.
Under API (Enable OAuth Settings),
select Enable Client Credentials Flow.
When you understand the security
risks, accept the warning.
Save your changes.
Although there’s no user interaction in the client credentials flow,
Salesforce still requires you to specify an execution user. By selecting an
execution user, you allow Salesforce to return access tokens on behalf of this
user.
From the connected app detail page, click Manage.
Click Edit Policies.
Under Client Credentials Flow, for Run As, click Magnifying glass icon, and
find the user that you want to assign the client credentials flow.
Here are the fiver major steps involved in client Credential Flow in
Salesforce.
- The connected app sends its client
credentials to the Salesforce OAuth token endpoint via a POST request.
- Salesforce validates the client credentials
and authenticates the app.
- Salesforce returns an access token on behalf
of the integration user you assigned.
- The connected app uses the access token to
call a Salesforce API, such as REST API.
- The API responds with the requested data for
the report.
Here’s an example POST request with the client credentials in the request
body. To request an access token, the connected app sends the POST to the
Salesforce token endpoint.
POST /services/oauth2/token HTTP/1.1
Host: MyDomainName.my.salesforce.com
grant_type=client_credentials&
client_id=*******************&
client_secret=*******************
where,
grant_type: The OAuth 2.0 grant type that the connected
app requests. The value must be set to client_credentials.
client_id: The connected app’s consumer key.
client_secret The connected app’s consumer secret.
If the request is verified the response will be
returned in below format.
{
"access_token": "*******************",
"instance_url":
"https://yourInstance.salesforce.com",
"id":
"https://login.salesforce.com/id/XXXXXXXXXXXXXXXXXX/XXXXXXXXXXXXXXXXXX",
"token_type": "Bearer",
"scope": "id api",
"issued_at": "1657741493799",
"signature": "c2lnbmF0dXJl"
}
Very Useful! Previously, I struggled quite a bit. But the guide has finally solved my problem.
ReplyDelete